|
Patches incoming for Bluetooth bug that could affect Apple, Intel, Broadcom, and some Android devices. A cryptographic bug in many Bluetooth firmware and operating system drivers could allow an attacker within about 30 meters to capture and decrypt data shared between Bluetooth-paired devices.
0 Comments
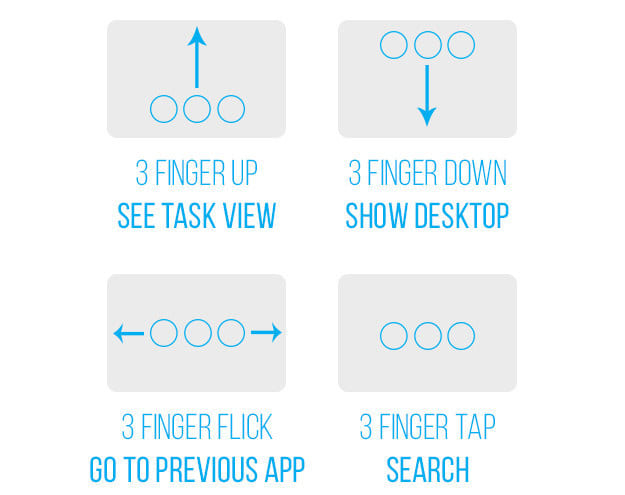
I’m sure most Mac users know Command-C means copy and Command-V means paste, but there’s a host of other useful shortcuts that make a Mac user’s life much easier. I’ve assembled this short collection to illustrate this truth: The Internet has quickly become the frontline in an ongoing battle with industrial espionage, sabotage and cyber terrorism. This results in lost revenue, stolen data, service interruptions and damaged reputations. Prepare for attack!!! Follow these 7 rules to protect your organization.. Ransomware can bring your business operations to a halt, encrypting sensitive data, and forcing you to pay the attacker to regain access. Keeping your organization safe requires a fundamental shift toward prevention, and away from simply detecting and requiring remediation after infection. The right architecture can make prevention real, and you can use this checklist to implement a true prevention-based platform. Its summertime and everyone is traveling. Have you considered your digital security while you travel? We have some tips to keep you safe so you can have a Bon Voyage. 1. Click the active (front most) window and move it left and right with your mouse. 2. They make navigation so much easier, but they only work on precision touchpads (like the ones on Surface tablets). First, check to see if your laptop has precision touch by going to Settings > Change PC Settings > PC and devices > Mouse and touchpad. You should see Your PC has a precision touchpad. Then you can try 3 finger swipe up to see "task view," which shows you all open windows. 3. Three finger swipe down: Show desktop. 4. Three finger flick left or right: Return to previous app (left) or go back to current app (right) 5. Three finger tap: Opens Cortana Search.
Is your internet moving a little slower than usual? Are you seeing hints of devices you don't recognize in Windows Explorer, or when you cast media to your TV? If you suspect a neighbor is stealing your Wi-Fi, here's how to check (and boot them off).
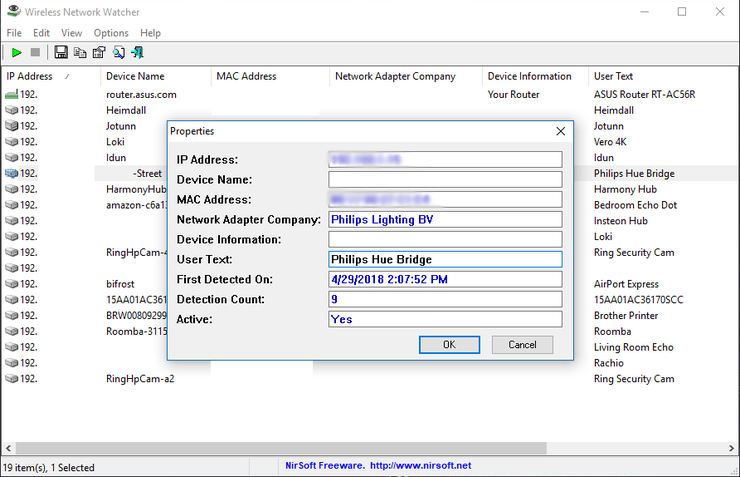
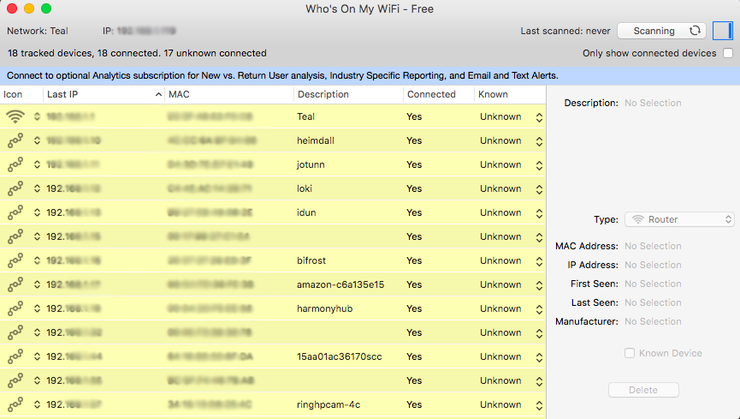
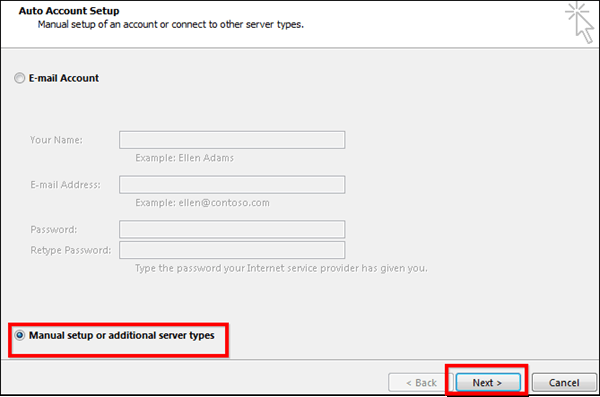
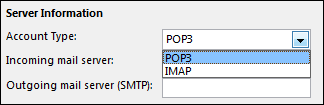
"So someone's watching Netflix on my internet," you may say. "What's the big deal?" Even if you have a little bandwidth to spare, you probably don't want other people on your network, especially if it's unsecured. If someone has access to your network, they have access to all the computers on that network, and that's dangerous. They could access files you're unknowingly sharing, they could infect you with malware, and in certain situations they could even steal your passwords and other personal information. As a result, you should take care to make sure each device connected to your network is one you can trust. Thankfully, there are free tools that'll help you see everyone on your Wi-Fi right now. See Who's On Your Network Windows users can download a free, portable program called Wireless Network Watcher (scroll down to the Zip download link below "Feedback" to get it), and Mac users can download a free, slightly more complex program called Who Is On My WiFi from the Mac App Store. Both tools will provide a list of every device currently connected to your network, so you can identify the ones that belong to you. Wireless Network Watcher To use Wireless Network Watcher, just launch the program, and it will immediately begin scanning your network. This will take a minute or two—you'll know it's working if the bottom-left corner reads "Scanning..." Once it's done, that message will disappear, and you'll be presented with a full list of connected devices. Find Users The resulting list may look a little cryptic, especially if you aren't super tech-savvy, but don't worry. You can ignore the IP address and MAC address listings for now. If you're using Wireless Network Watcher, just focus on the "Device Name" and "Network Adapter Company" columns. For example, I see an item named "Dulce" in Wireless Network Watcher, which is the name of my wife's MacBook. I see another with no name, but with "Philips Lighting BV" as the network adapter manufacturer, which means it's probably the hub for my Philips Hue lights. You can double-click on a device to add "User Text" that helps you identify each device, which will help you narrow down all the items in this list. If your organization uses a Google Apps account to handle email and you’re an Outlook 2013 user, it makes a lot of sense to configure that account to send and receive email through Microsoft’s email client. That way, it’s much easier to never miss an important email and answer it the second it comes in. Configuring Outlook 2013 to work with your Google Apps email account isn’t too difficult, as long as you follow the steps below exactly. GOOGLE APPS EMAIL IN OUTLOOK 2013 Step 1: Start Outlook 2013 and click File in the top menu of Microsoft’s email client. Step 2: Make sure Info is selected in the menu on the right side of your Outlook 2013 window (not the Options one you used when enabling the Auto Complete feature). Step 3: Let’s start configuring your account. In order to start doing this, click the Add account button. Step 4: I probably don’t need to mention this, but I will anyway: the next step requires you to have your Google Apps email account username and password close by. You’ll need them for it. Set the configuration process to Manual setup or additional server types and then click the Next button. Step 5: Select POP or IMAP in the window that comes up, then click Next to proceed to the next step.
Step 6: This is the fun part, the one where you fill in all the settings needed. Worry not, if you do it right, it’s the last time you’ll be required to go through it (at least for this email account). Start by setting the email account to IMAP, under Server information, like I did in the screenshot you’re seeing below. |
Archives
August 2018
Categories |














 RSS Feed
RSS Feed

