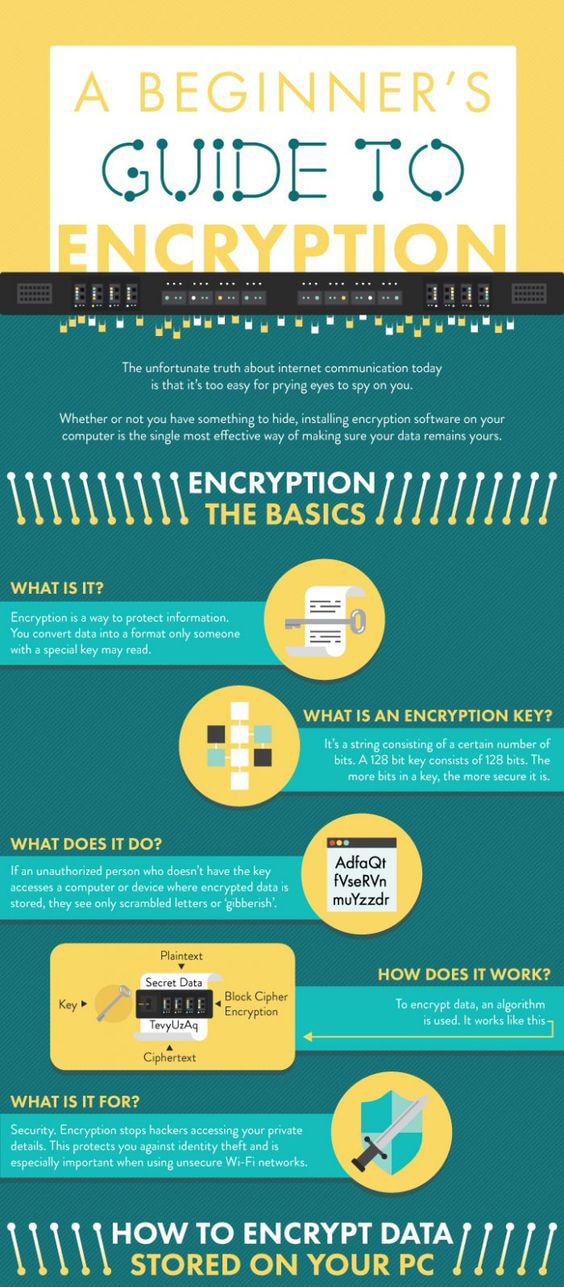
|
Phishing attacks skyrocketed in the financial services industry and IT sector early this year, according to the Spam and Phishing in Q2 2018 report from Kaspersky Lab. Over a third (35.7%) of phishing attempts were in the financial services industry, with the IT sector coming in second at 13.83%, according to the report. One of the most popular and easiest methods of cyberattack, phishing is not a new attack vector used by cybercriminals on businesses. In fact, more than half (54%) of companies receive phishing emails regularly, leaving companies at a constant threat of attack. Phishers especially targeted finance companies last quarter, attacking banks, e-shops, and payment systems, according to Kaspersky Lab. The focus on money theft should not only encourage users to protect their finances, but also protect their data as they navigate online banking systems, said the press release.
0 Comments
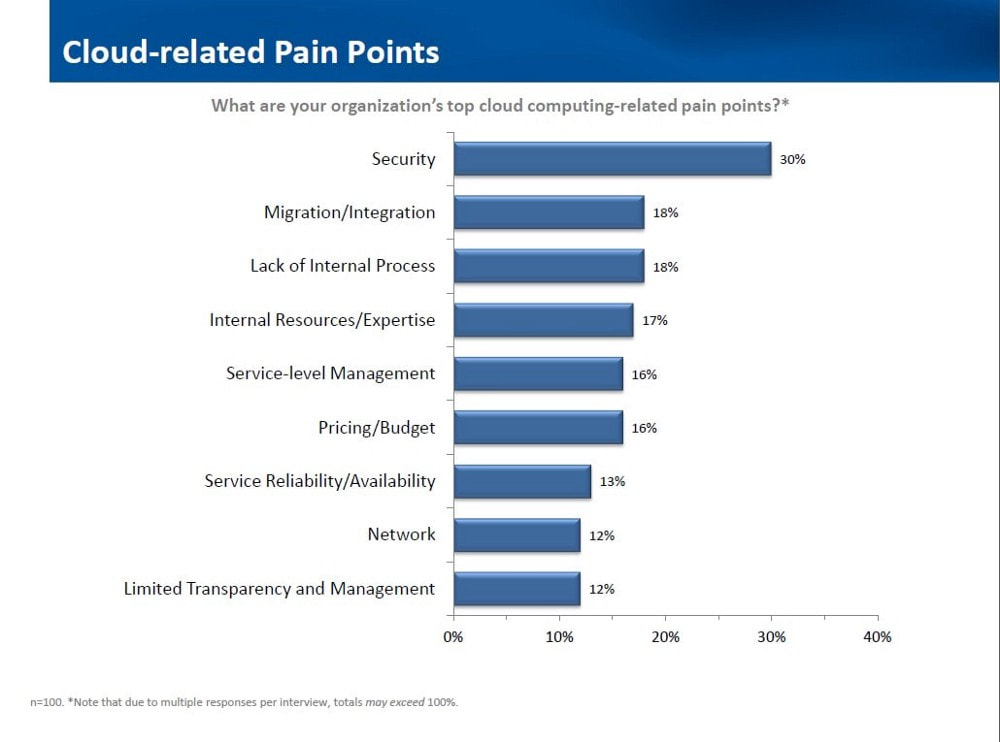
So you’ve decided you want to move your services to the cloud. Congratulations! That’s a great decision that will help take you and your business and applications to the next level for so many reasons. However, the cloud migration process can be painful without proper planning, execution, and testing. A survey found that only 27% of respondents were extremely satisfied with their overall cloud migration experience. On a list of the most common cloud-related pain points, migration comes right after security. In reality, these points are all related to each other. By having a solid plan and great execution, most of these common problems will be solved before they have the chance to cause you any pain. To make sure things go well for you, I’ve made this cloud migration checklist to help you avoid common mistakes. OVERVIEW This checklist for cloud migration strategy can be broken down into four main parts:
If you follow each of these steps, it should be a fairly smooth process. Each stage has its own questions to ask and steps to follow. Let’s take a look at each section in more detail. Webcams may give you a window on the world, but they also offer criminals a view into your private life. Here’s what you can do to stop yours being hijacked. The picture of tape covering the web cam on what’s believed to be Facebook founder Mark Zuckerberg’s computer sparked lots of debate about the safety of personal webcams. You may not use the webcam built into the top edge of your laptop screen, but how do you know someone else isn’t secretly using it to spy on you? It may sound far-fetched, but in 2014 a Russian website carrying video captured illegally from 500 UK webcams was exposed, while in 2015, a British hacker was convicted of spending up to 12 hours a day spying on people by hacking their webcams. Fortunately, there are some simple steps you can take to make sure your webcam can’t be hacked in this way. With talk of a tech talent shortage, a new report reveals just how many tech jobs are being created in 2018. In July, the US IT sector experienced the best month for industry growth so far in 2018, with an estimated 14,500 jobs added that month alone, according to a Friday report from CompTIA. So far this year, the IT industry workforce has expanded by an estimated 71,800 jobs, the report noted. |
Archives
August 2018
Categories |








 RSS Feed
RSS Feed

