|
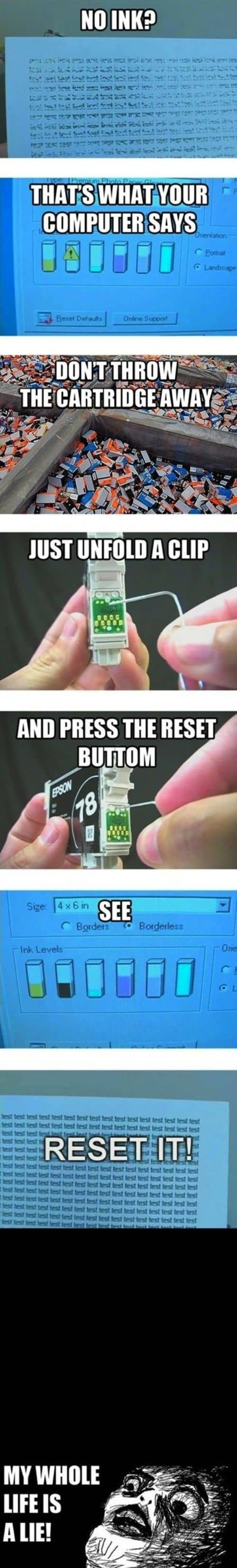
1. Make it look like you're busy and important.  2. Use a piece of Scotch tape to clean your keyboard. 3. Or a Post-it Note 4. Or a Q-tip. 5. Reupholster a boring desk chair. 6. Make quick and easy iced coffee using the office hot brew. 7. Use binder clips to keep all your cords neat. 8. Or use a kitchen basket to secure cords on the underside of your desk. 9. Fix a scuffed shoe with a Sharpie. 10. Make your stapler detachable so you can staple in the middle of sheets. 11. Clip your coffee cup to the edge of your desk to save space. 12. Make drawer organizers from cardboard or cereal boxes. 13. Air horns + office chairs = minutes and minutes of gleeful cackling at the expense of your coworkers. 14. Same with jeans and shoes. 15. Add a pocket to a tie for secret and convenient storage. 16. Store small office supplies in a cheap spice rack. 17. Make eating at your desk even easier with pen cap utensils. 18. Ensure that nobody ever steals your sandwich from the communal fridge again. 19. Or forgo dealing with the fridge entirely. 20. Try a sponge as a genius alternative to an ice pack in your lunch. 21. Use a spring to keep a papers organized. 22. Replace your boring water cooler with something more interesting. 23. Clean up crumbs with a mini USB vacuum. 24. Keep a pair of reflective sunglasses on your desk so you can tell when someone is coming up behind you. 25. And if you're being monitored yourself, show that camera what's what. 26. Use a connector cord to run your headphones under your desk instead of over your keyboard. 27. Take a leaf out of George Constanza's book and make a desk-bed for a lunch time cat-nap. 28. Eke out the last bits of ink from a seemingly empty cartridge. 29. Keep yourself on a water-drinking schedule. 30. Multitask. :)
0 Comments
If you want the best possible Wi-Fi performance in your home or small business, follow these simple steps for setting up your router and wireless network the right way. Beyond Basic Setup If you've ever purchased a new PC, you know there's more to setting it up than just taking it out of the box and turning it on. The same is true of your home router. Putting together a home network isn't trivial, but it doesn't have to be overly difficult, either. Hardware manufacturers are making it easier than ever for even non-technical users to put together home networks. New routers come with clearly labeled ports, in some cases, color coded, making it simple for users to connect everything. Most routers have a basic configuration preset at the factory, which simplifies things even more. And networking manufacturers are aiming to make things even simpler with mesh-based Wi-Fi systems like Eero and Google Wifi, which are geared toward extreme ease-of-use, offering fast, seamless app-based set up. But just because you've plugged everything in and it seems to be working doesn't mean your network's performance and security are as good as they could be. Follow these basic steps to properly configure your wireless router and optimize your wireless network and connectivity. Selecting the Right Router The heart of your home network is your router. So it's worth investing time researching your options before deciding on one. Depending on your current router's age, you don't necessarily need to upgrade to new hardware. If your router is more than a few years old, however, it may only support WEP for security—if so, upgrade right away. WEP is no longer secure. Large ISPs such as Comcast and Verizon typically provide customers with routers as opposed to modems. The majority of these models are less feature-rich than the routers you could purchase on your own. Also, some ISPs make it difficult for customers to access the configuration interface. Some ISPs even charge you extra if you want to use certain features. For example, Spectrum (formerly Time Warner Cable) in New York charges users for turning on the router's built-in Wi-Fi network. Alas, you should buy your own router. Getting Online Now that you have a router, you need to get it connected and online. If your service provider gave you a modem when they activated your internet service, this should be pretty simple. Just follow these steps:
If you are using an ISP-supplied router instead of a modem, things are a bit more complicated. First, you reconfigure the ISP's router to operate in bridge mode before you connect it to your new router. Bridge mode means the old router doesn't do anything to the network traffic and just passes it along to your new router for processing. While you can do this on your own, some providers will do it for you remotely once you make the request. Once the ISP supplied router is in bridge mode, just follow the above steps to get your new router online. Accessing the Management Console With the router and PC physically connected, you can now begin customizing the router's configuration. Most routers these days are managed via a web browser or a mobile app and are shipped using a default IP address, administrator account, and password. This default IP address will vary from vendor to vendor, so check your documentation to find out yours. Once you have that information, accessing the management console is easy.
Change the Password and Upgrade the Firmware The very first thing you should do is change the router's default password. This may seem obvious, but you'd be surprised how many people don't do this. Keeping the default password compromises the security of your entire network and can leave your router exposed to anyone. The next thing to do is to make sure your router is running the latest firmware released by the manufacturer. This is a good practice because you never know how long a product has sat on a shelf before it made it into your hands. Also, firmware updates can address many potential issues before you ever encounter them. This process will vary by vendor; check your documentation for details. Managing Your IP Addresses With DHCP Next it's time to focus on your router's LAN configuration. As I previously mentioned, DHCP, which manages all the IP addresses on your network, is typically enabled by default on most consumer routers. Your router uses the IP address, a numeric identifier, to locate your PC and route the correct network traffic. If the computer or mobile device does not already have an IP address, it will request one from the network's DHCP server, which is on the router. The DHCP server pulls an IP address from a pool of available IP addresses (called a Scope) and assigns it to the device. When the device disconnects from the network, or a certain amount of time has passed (referred to as a lease) the IP address returns to the DHCP pool. Certain devices, such as servers and printers, need to always have the same IP address. They can't have their addresses change periodically. If you are in that situation, you need to assign a static IP address, an IP address that never goes in the DHCP pool and is assigned to the device permanently. To make static IP addresses available, we exclude some IP addresses from the DHCP scope so they can be assigned manually. To set the DHCP scope, follow these steps:
Working With Static IPs Now that you have some IP addresses available, you'll need to manually assign them to devices that need static addresses. What you need to do is to provide the network adapter of your device with a unique IP address, the network Subnet Mask, the Gateway address and a DNS server address. Based on the above example, you could use any address between 192.168.0.52 and 192.168.0.254 for the IP address and 255.255.255.0 for the Subnet Mask. The Gateway and DNS address is the same as the router's IP address; which is 192.168.0.1. Just be sure to keep a list of the static IP addresses you've assigned already so that you don't reuse them again by mistake. The process for assigning a static IP address to a network adapter will vary based on the device you're trying to configure, so check your documentation. Activating Your Wi-Fi With your network now properly configured you can move on to setting up your wireless network. This is actually very simple and should only take you a couple of minutes. When you do this, make sure you use a computer that is connected to the network via an Ethernet cable. If you try to configure Wi-Fi over wireless, you'll lose the connection to the management console whenever changes to the configuration are applied. Now follow these steps:
...Speaking of Security Many routers support Wi-Fi Protected Setup or WPS, which is a network security standard that attempts to secure a home network easily via the press of a button. Disable it. Researchers have found WPS can be vulnerable to brute-force attacks. For the marginal convenience it provides, WPS just isn't worth the potential for compromise. As an additional security measure you can disable the SSID from broadcasting. By doing this you make the network undiscoverable to wireless devices that are looking for available wireless networks. This will hide your network from all wireless devices, including your own. In order to connect to your network, you'll need to enter in the SSID manually into each device. While this is by no means foolproof security, it will keep your network concealed from more casual users. Depending on your router, the wireless configuration screen may include the option to enable a guest network. The Guest Network allows visitors to your home to get online while isolating them from the rest of the devices in your network. This is a useful option and we would recommend using it. Guest networks are available on both the 2.4GHz and 5GHz networks. Configure it the same way you did your regular wireless network, but be sure to assign it a different passphrase. Sharing Your Data One of the most important aspects of a home network is the ability to share network resources. There are a variety of ways to accomplish this. A server is the best solution, but not many home users will have one. Network Attached Storage or NAS devices are more cost effective and easier to use in this environment. As an alternative, many routers have built-in USB ports which can be used to share hard drives or printers among all network users. Windows PCs also allow you to share data among network users. There are a few different ways to accomplish this, but the simplest by far would be to use a Homegroup. The Homegroup is quick and easy to set up and allows you to share data with all or some network users. It can even be password protected. What's Next? As any IT professional will tell you, this is just the tip of the iceberg. There are dozens of additional features within your router that would help to make your network more secure and perform better. These include Quality of Service, better known as QoS, for prioritizing network traffic, and Universal Plug-n-Play, which allows devices like media servers to communicate easily with other PCs on the network. There's also port forwarding, dynamic DNS, remote management, and so much more. If you need any help with any of this contact Hands of Support Computer Service
Data Privacy Day (DPD), is an annual international effort to promote the importance of data privacy. DPD is sponsored in the United States by the National Cyber Security Alliance (NCSA) with the theme, Respecting Privacy, Safeguarding Data, and Enabling Trust. In honor of this day we bring you: "SafeGuarding Your Data"Why isn't "more" better?Maybe there is an extra software program included with a program you bought. Or perhaps you found a free download online. You may be tempted to install the programs just because you can, or because you think you might use them later. However, even if the source and the software are legitimate, there may be hidden risks. And if other people use your computer, there are additional risks.
These risks become especially important if you use your computer to manage your personal finances (banking, taxes, online bill payment, etc.), store sensitive personal data, or perform work-related activities away from the office. However, there are steps you can take to protect yourself. How can you protect both your personal and work-related data?
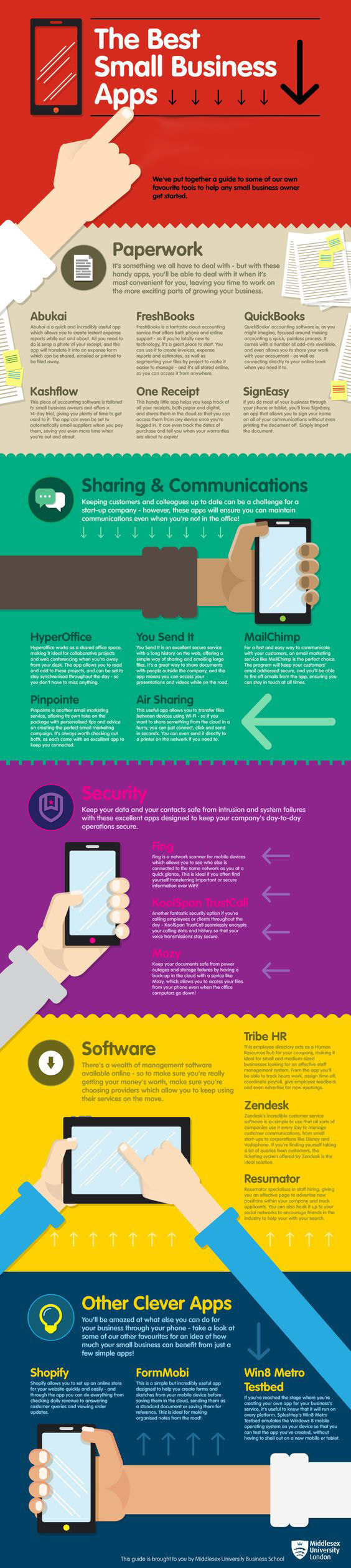
Nowadays, small businesses can get much of their work done right from their computer, laptops and even on a smartphone with easy to use programs and applications. Here are top 20 apps and tools to help any small business owner get started. We've put together a guide to some our own favorite tools to help any small business owner get started. *see Infographic for all the details.
Paperwork Its something we all have to deal with - but with these handy apps, you'll be able to deal with it when its most convenient for you, leaving you time to work the more exciting parts of growing your business.
Sharing & Communications Keeping customers and colleagues up to date can be a challenge for a start-up company - however, these apps will ensure you can maintain communications even when you're not in the office!
Keep your data and your contacts sage from intrusion and system failures with these excellent apps designed to keep your company's day to operations secure.
There's a wealth of management software available online - so to make sure you're really getting your money's worth, make sure you're choosing providers which allow you to keep using their services on the move.
You'll be amazed at what else you can do for your business through your phone - take a look at some of our other favorites for an idea of how much your small business can benefit from just a few simple apps.
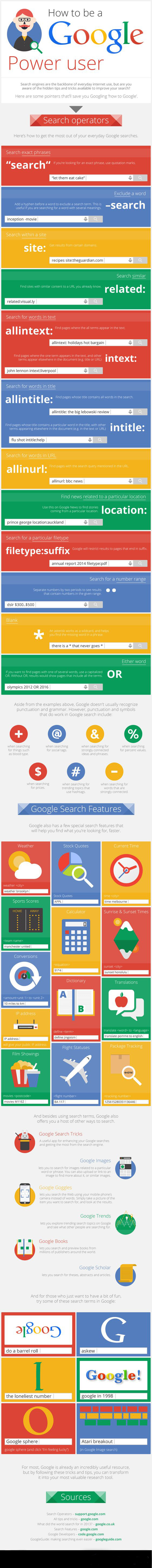
We’ve all been there. You type in an exact, specific, and seemingly perfect search term into Google hoping to get answers to your query only for the search engine to return nothing. Or rather, with everything. How are we supposed to find exactly what we want if there are millions of results for every little word or phrase we search? Well, we have our ways.
Search engines are the backbone of everyday internet use, but are you aware of the hidden tips and tricks available to improve your search? Here are some pointers that'll save you Googling 'how to Google'. Search Operations Here's how to get the most out of your everyday Google searches. Search exact phrases Exclude a word Search within a site Search similar Search for words in text Search for the words in title Search for words in URL Finds news related to particular location Search for a particular filetype Search for a number range Blank * Either word Check out the infographic for Google Search Features and other ways to search including Google search tricks, Google Images search tips, Google goggles, Google Trends, Google Books and Google Scholar plus a few fun tricks below.
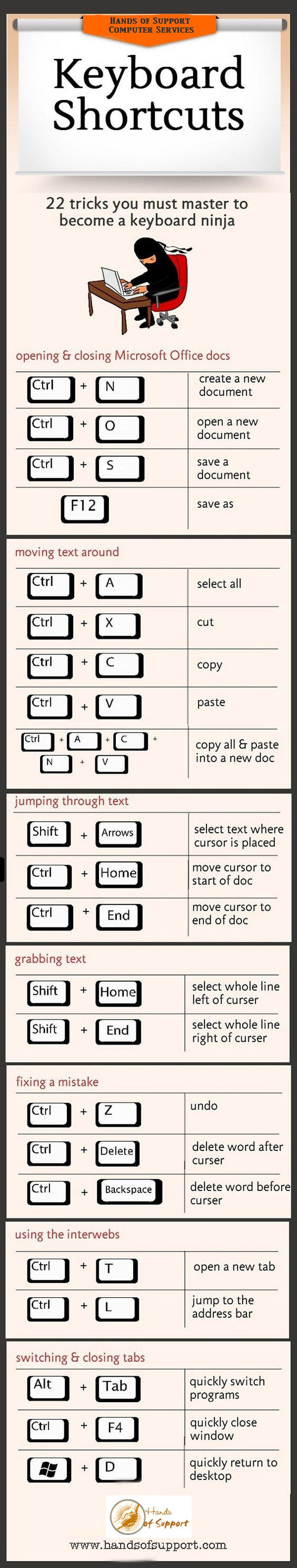
Learn the tips that make you a wiz at working in Microsoft Office. Toggle quickly and learn to master Keyboard Shortcuts in Microsoft.
We are in the one of the hardest hitting flu seasons ever! So its important to know how to keep from getting sick. When you learn where the germs are hiding then it helps you from getting the flu. Learn the do's and don'ts on arming yourself this cold and flu season.
1. 5G
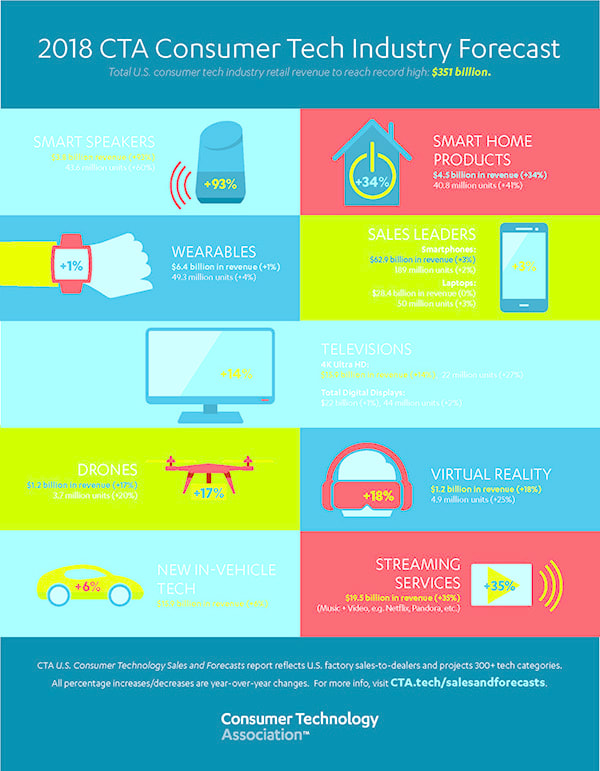
5G is a type of wireless technology that you may have heard about in recent headlines -- such as Verizon selecting Samsung as the provider for its 5G commercial launch. One reason why it's such a big deal is that it will result in higher wireless speeds, capacities, and lower latency -- which generally means that there will be far fewer delays or "technical hesitancies" in some of the things it powers, like wireless VR or autonomous vehicles. That benefit is two-fold. Not only does it enrich a user experience when it comes to something like AR or VR by providing higher data rates, but it's also practical for safety -- which is where the latency piece comes in. As Koenig explains, one of the key pieces of autonomous driving technology safety is the ability for it to independently make operational decisions -- quickly, and perhaps more seamlessly than a human driver could. But just how fast is 5G? During the presentation, the example of a two-hour movie download was used. On a 3G network, for example, that would take 26 hours. On 4G, it would be lowered to six minutes. But on 5G, it's lowered to 3.6 seconds. 2. Artificial Intelligence We've talked a lot about this one, and it came up in some of the major press events of 2017. A considerable amount of attention will be paid to the role of AI in digital personal assistants, which plays into the smart home sector. There, AI technology like machine learning lends itself to the ability to recognize user preferences and behavioral patterns. Smart speakers, for example, were named as some of the heaviest hitters in the CTA's Consumer Tech Industry Forecast, with a predicted revenue of $3.8 billion (an increase of 93%), and 43.6 million units sold (+60%). Within this realm, AI also plays a major part in autonomous driving capabilities -- especially when it comes to sensory perception (like objects in the vehicle's path), data processing, and action. That, too, was a key piece in the industry forecast, with $15.9 billion revenue predicted, or 6% growth. What's next? Two key things to come were identified, the first being conversations with context -- like machines carrying on conversations with humans with better natural language processing, to make it more like the way we speak to each other. The second is the ability of AI to build trust and reduce bias with users -- which, when executed successfully, can help AI systems do things like explain why it makes certain recommendations of actions or content. 3. Robotics Robotics, in this context, seemed to play the biggest role in consumer electronics -- which seems fitting, seeing as CES is largely about the newest technology in that sector. The speakers seemed to take a particular interest in Kuri, a robot that was described as a "family friend" that can "capture life's moments automatically using face recognition." It's a bit nostalgic of the Google Clips photo technology announced last fall, which boasts allowing users to spend more time in the moment, rather than taking the perfect picture, with similar recognition technology. The event also shed light on Honda's robots, which are engineered around what it calls its "3E Philosophy," built on the pillars of empowerment, experience, and empathy. It reflected a pattern of working to incorporate more empathy into robotics -- like Kuri, these would be moving, speaking computers with feelings. 4. Voice: The Fourth Sales Channel The CTA's research has shown that one in four shoppers used voice assistants in their holiday shopping during the 2017 season. Here's an area where marketers can use the rise in smart speaker sales (and its anticipated continued growth) to their advantage. Voice assistance and technology are becoming larger parts of a brand's identity -- an area of opportunity for those who have not yet begun to leverage it as such. So, how can marketers do that? I recommend looking into ways to merge your brand with voice assistants and see how you can create content exclusively for that medium -- for example, something like building a custom, branded skill for Amazon Echo. 5. Facial Recognition on the Go From the iPhone X Face ID technology to your car being able to recognize your eyes and nose, our faces are playing a greater role in helping our devices recognize us and capture our preferences -- anytime, anywhere. And, it seems, we're becoming more comfortable with it. According to the CTA's research, users have a growing amount of trust in this technology being used for such personal data as medical information. But it's also often a matter of convenience -- as a video shown later in the day by NVIDIA indicated, face recogniton can be used by smart vehicles to recognize its owners for unlocking doors, opening trunks, and more. All of these patterns are reflected in the anticipated uptick for in-vehicle technology -- revenues this year are predicted to reach $15.9 billion, which is a 6% increase. 6. Virtual Reality VR isn't exactly a new trend, but what I'll be keeping our eyes on is the newest use cases for it. Content, it's predicted, is where the most noticeable change and evolution will take place, especially when it comes to creating immersive experiences for brand awareness. Where once this technology was almost exclusively used to tell a story for the purpose of entertainment, businesses and organizations are now presented with an opportunity to leverage VR for commercial purposes -- like shopping, for example, or a deeper look inside what helps a business run and create its products or services. Augmented Reality (AR) is further working its way into the B2C space, as we enter the era of what was called "AR for all." There have been several consumer-oriented use cases from brands like Ikea and Wayfair -- using the technology for things like home decor -- as well as demonstrations on how it enhances a gaming experience from both Apple and Google. But AR first made a name for itself in the B2B sector -- largely for purposes related to trade shows and enhancing information delivery to analysts. And as it continues to grow its presence within the consumer sector, I don't anticipate it leaving B2B behind. As the technology improves, many of the purposes it was originally used for will also continue to evolve, presenting an opportunity for business-facing marketers. 7. Smart Cities From self-driving pizza delivery vehicles (seriously -- this is a thing) to environment and energy usage, smart cities are where society and technology intersect. While Smart Cities fill a new enough category that their roles in marketing remain fairly open-ended, they do present an opportunity for brands looking to increase their roles in the community -- especially where technology is concerned One of the best cases for the growth of Smart Cities, for example, is how they will work to bolster public safety and services -- something that cannot happen without the cooperation of the market, organizations, and regional leadership. By exploring where their own organizations fit into the ecosystem of a Smart Cities, marketers can work ahead of the curve by looking for ways their brands can actively support and contribute to a Smart City, thus playing a larger role in what remains, for now, an emerging trend. |
Archives
August 2018
Categories |

































 RSS Feed
RSS Feed

