|
Dear Hands of Support,
My computer's feeling a little sluggish lately and I want to boost its performance if possible. Are there any easy and reliable tools I can use to check my PC and tune it up? Thanks, Hoping for a Boost Dear Hoping, Getting top performance out of your computer is definitely a challenge. We've got some ideas for you that may help. Perform Basic Maintenance We guess that you're already doing basic maintenance for your computer. Performing those maintenance steps, such as keeping your operating system and applications up to date and cleaning out temporary files, should keep your system running well. Sometimes, just deleting bloatware can really make a big difference in your computer's performance (we recommend PC Decrapifier for the job). So definitely the first thing we'd recommend is to check the guide for your operating system. If you're a Mac user don't forget to use the built in Disk Utility feature every 3 months. Download and Run Diagnostic Tools Like Soluto to Identify ProblemsIf your computer is experiencing problems, however, like applications freezing or serious slowdowns, you can use computer diagnostic software to troubleshoot the problem. One computer diagnostic software is Solute. Solute is a free Windows tool that shows you which applications may be slowing your system down. It's also a tool for solving application crashes before they happen and can report crash information based on other Solute users' experiences. Perform a Quick System Check Up Online with PC PitStop OverDrive If you just want a quick PC health check, however, there's a free online tool called OverDrive from PC PitStop you can use that will analyze your computer's hardware, software, security, and so on, and give you recommended fixes, if any. The site looks spammy, but the tool actually does a good job of analyzing your system and can also be used for benchmarking your computer. (Note: PC PitStop also offers PC Matic and other software downloads that can check your computer's performance, but you don't need to download and install any software to run the OverDrive tests.) When it's done scanning, OverDrive will suggest fixes like clearing your cache, updating any missing drivers, increasing security settings and so forth. Re-run the tests after making any suggested fixes and you should see your rank improve and your PC operating at least a bit better. Good luck and have fun testing your system! Sincerely, Hands of Support
0 Comments
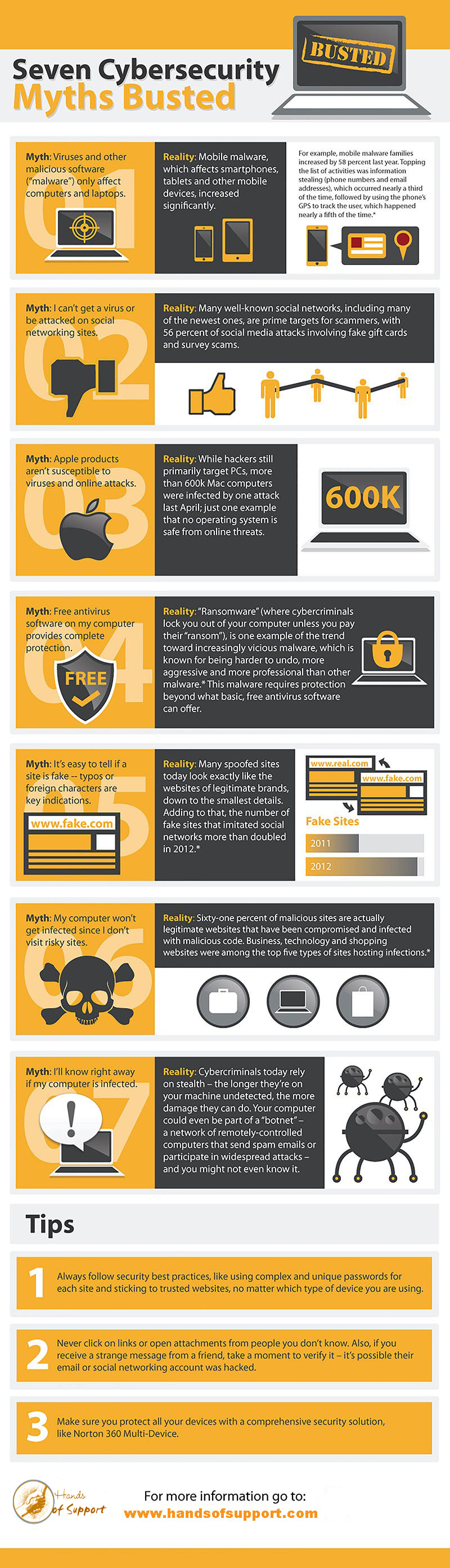
It’s a common occurrence these days—one of your friends recently had an online account hacked but doesn’t have a clue how it happened. We’ve all heard tech advice from a tech-savvy sister or the IT guy at work, but what’s the truth? When it comes to online security, it’s sometimes difficult to discern between perception and reality.
Online threats are changing and becoming more sophisticated. Last year, we saw constant and continued innovation from cybercriminals. For example, there were more online attacks taking advantage of previously unknown security gaps than any year before; attacks continued to spread across an increasing number of popular social networks, and cyber and industrial espionage is now a reality. With a constantly changing online world and security landscape, it seems most people are still confused about existing threats and their impact, as well as what they can do to protect themselves. Luckily, Hands of Support Computer Services is here to help keep you secure with computer saving info.
Losing arguments with your spouse? Missing out on raises at work? Maybe you need to improve how you're approaching these conversations. Learn how you can use simple psychological tools to your advantage in nearly any type of interaction,
1. Give others Power 2. Ask for more than you want 3. Stop Talking 4. Emphasize the Pay off 5. Ask for Help 6. Be the first to sacrifice 7. Timing is Everything 8. We're in this together 9. Get angry - sometimes It seems obvious, but passwords are our first line of defense against a growing army of nefarious hackers looking to steal our data, money or even identities. While many people know how serious the issue of cybersecurity is, many still use passwords that are remarkably bad. Compounding matters is the common practice of using the same password across multiple accounts, so a hacker who gains access to one account may be able to breach others. But protecting yourself is easy and there’s just no excuse for leaving your accounts vulnerable with bad passwords.
With more and more of us shifting everyday tasks—banking, education, social interaction, even shopping for groceries—to the virtual world, securing our personal information has become more important than ever. One of the simplest ways to help protect our financial and other info from prying eyes and would-be identity thieves is to use a strong password. Yet many people take a decidedly casual approach to choosing a password, with potential disastrous results. Much of the advice in the graphic might seem like common sense, but the frequency with which password-related breaches occur tells us that’s not the case. There are also some interesting things in there that you might not know, however. For example, the length of your password is incredibly important — a hacker can use a “bruteforce” attack to guess a 10-character password in about 1 week, while a 15-character password will take almost 1.5 million centuries to crack. Do yourself a favor and look through the infographic below for helpful hints on how to protect yourself online. Essential Tips that Every Mac owner should know. There's always one...But are your employees' faults always their fault? We're probably all little bit one of these. Here's how to turn them into well-oiled components in your team.
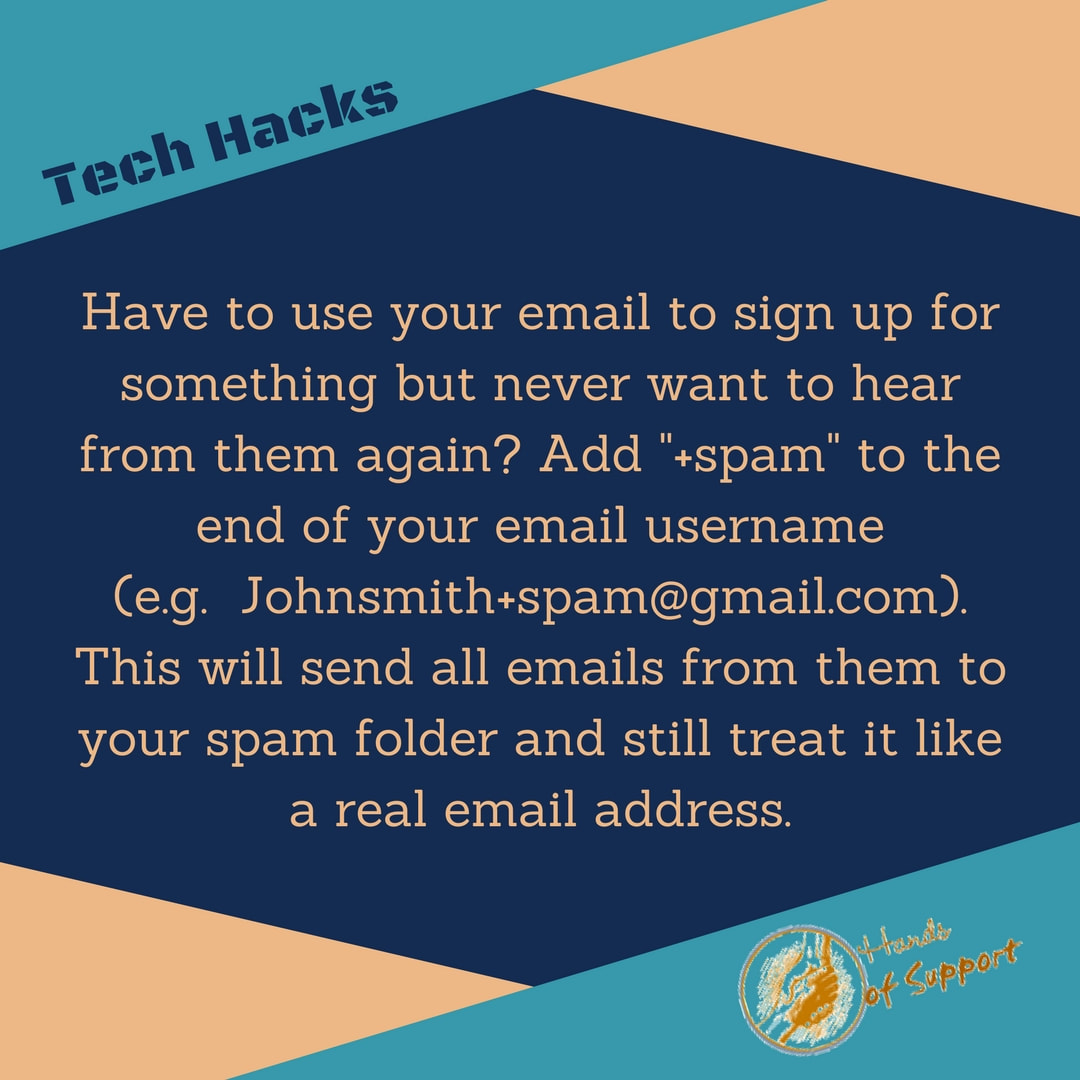
Click here to receive a new Tech Hack every week.
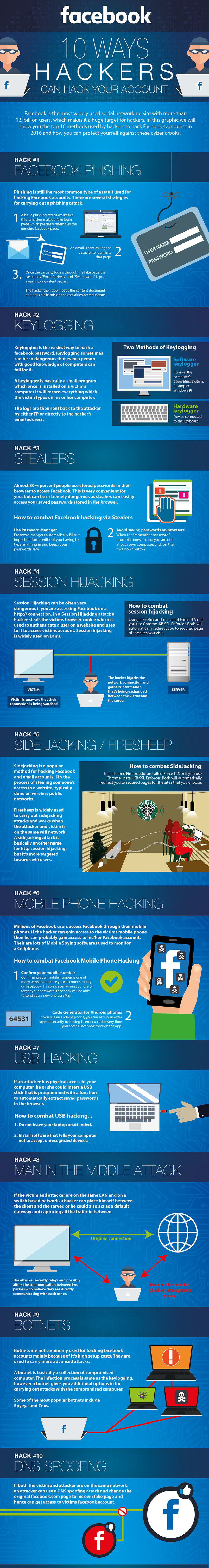
Facebook is the most widely used social networking site with more than 1.5 billion users, which makes it a huge target for hackers. In this graphic we will show you the top 10 methods used by hackers to hack Facebook accounts and how you can protect yourself against these cyber crooks. Hack #1 Facebook Phishing
Phishing is still the most common type of assault used for hacking Facebook accounts. There are several strategies for carrying out a phishing attack. 1. Basic Phishing attack works like this...a hacker makes a fake login page which precisely resembles the genuine Facebook page. 2. An email is sent asking the casualty to login into that page. 3. Once the casualty logins through the fake page the casualties "email address" and "secret word" is put away into a content record. The hacker then downloads the content document and gets his hands of the casualties accreditations. Hack #2 Keylogging Keylogging is the easiest way to hack a Facebook password. Keylogging sometimes can be so dangerous that even a person with good knowledge of computers can fall for it. A keylogger is a basically small program which once installed on a victims computer it will record everything which the victim types on his or her computer. The logs are then sent back to the attacker by either TP or directly to the hackers email address. Hack #3 Stealers Almost 80% percent people use stored passwords in their browser to access Facebook. This is very convenient for you, but can be extremely dangerous as stealers can easily access your saved passwords stored in the browsers. How to combat Facebook hackers via Stealers 1-Use Password Manager Password managers automatically fill out important forms without you having to type anything in and keeps your passwords safe. 2-Avoid saving passwords on browsers When the "remember password" prompt comes up and you are not at your own computer, click on the "not now" button. Hack #4 Session Hijacking Session Hijacking can be often very dangerous if you are accessing Facebook on a http://connection. In a Session Hijacking attack a hacker steals the victims browser cookie which is used to authenticate a user on a website and uses to it to access victims account. Session hijacking is widely used on Lans. How to combat session hijacking Using a Firefox add-on called Force TLS or if you use Chrome, KB SSL Enforcer. Both will automatically redirect you to secured page of the sites you visit. Hack #5 Side Jacking / Firesheep Sidejacking is a popular method for hacking Facebook and email accounts. It's the process of stealing someone's access to a website, typically done on wireless public networks. Firesheep is a widely used to carry out sidejacking attacks and works when the attacker and victim is on the same wifi network. A sidejacking attack is basically another name for http session hijacking, but it's more targeted towards wifi users. Hack #6 Mobile Phone Hacking Millions of Facebook through their mobile phones. If the hacker can gain access to the victims mobile phone then he can probably gain access to his/her Facebook account. There are lots of mobile spying softwares used to monitor a cellphone. How to Combat Facebook Mobile Phone Hacking 1- Confirm your mobile number Confirming your mobile number is one of many ways to enhance your account security on Facebook. This way, even when you lose or forget your password, Facebook will be able to send you a new one via SMS. 2- Code Generator for Android phones If you use an android phone, you can set up an extra layer of security by having to enter a code every time you access Facebook through the app. Hack #7 USB Hacking If an attacked has physical access to your computer, he or she could insert a USB stick that is programmed with a function to automatically extract saved passwords in the browser. How to combat USB hacking.. 1- Do not leave your laptop unattended. 2- Install software that tells your computer not to accept unrecognized devices. Hack #8 Man in the Middle Attack If the victim and attacked are the same LAN and on switch based network, a hacker can place himself between the client and the server, or he could also act as a default gateway and capturing all the traffic in between. Hack #9 Botnets Botnets are not commonly used for hacking Facebook accounts mainly because of its high setup costs. They are used to carry more advanced attacks. A botnet is basically a collection of compromised computer. The infection process is same as the key logging, however a bonnet gives you additional options for carrying out attacks with the compromised computer. Some of the most popular bonnets include Spyeye and Zues. Hack #10 DNS Spoofing If both the victim and attacker are on the same network an attacker can use a DNS spoofing attack and change the original Facebook.com page to his own fake page and hence can get access to victims Facebook account. Now you may not care if some anonymous company knows what sites your browser visited. This data is collected anonymously (well, semi-anonymously) and is designed to show you ads you might be more interested in than, say, how to reduce belly fat or get a cut rate loan. Many people, some of them diehard privacy advocates, prefer targeted ads. I'm here to tell you that this debate is not about advertising. It's about something much bigger and potentially much more profitable. It's about creating profiles of your behavior online and designing algorithms to make decisions about you based on that behavior. It's about gathering that data, mining it, and selling it to the highest bidder, over and over again. Today that data is used almost exclusively to deliver ads. But how will it be used tomorrow? 1. Oh the prices you'll pay Variable pricing exists in many forms outside the Internet. Anyone who's booked an airline ticket can tell you prices vary wildly depending on when you buy your seat. Soda at the convenience store next to the beach costs more than it does at the supermarket down the street. Bad drivers have to pay more for their auto insurance. Most people understand these things; they're all pretty obvious. But should you pay more for a hotel room just because you used an Apple device to search for it? You might. In fact, as the Wall Street Journal has reported, Mac users who booked hotel rooms on Orbitz paid an average of $20 to $30 a night more than those who visited the site using a Windows PC. They weren't charged more for the same rooms, but they were shown more expensive rooms – which they then booked. Why? Because every Web site you visit knows what operating system you're using. It receives that information automatically, along with other data that can be used to uniquely identify your machine, such as your IP address. (That's the semi-anonymous part I mentioned above.) Add profile data gleaned from behavioral tracking cookies, and the information they can use to decide what prices to show you becomes much richer. If you've provided your phone number or email address, they can add even more info about you, including data from public records databases and your offline purchase history. But Web sites don't need to know your name to determine what type of consumer you are. All they need to know is which demographic “buckets” you fit into. You'll never know you're being shown a different deal than your next door neighbor. And the data they use to make these decisions is not at all obvious. 2. You are more than the sum of your “Likes” A few months ago a group of Cambridge University researchers published the results of an experiment using a Facebook app that tracked everything its users “Liked” on the social network. They surveyed the app's users as to their demographic information, then plotted correlations between who they said they were and what they did on Facebook. Using just Facebook Likes, the researchers were able to determine with impressive accuracy a person's gender, age, race, sexual tendencies, political leanings, drug habits, and more. Some of the correlations were, frankly, strange: People who like curly fries tend to have higher IQs. Some made intuitive sense: Men who like the TV show “Glee” are probably gay. And some were both: Fans of the death metal band Slayer were more likely to smoke cigarettes. This is what data mining is about – making correlations between two or more seemingly unconnected bits of information. It's how tracking companies like ToneFuse know that John Lennon fans are more likely to own cats, or that Rhianna fans are good candidates for buying a cut-rate cruise. It's how the FBI and other three-letter agencies are hoping to track crooks and terrorists before they strike. In other words, you don't have to visit Marlboro.com for advertisers to detect your nicotine addiction. They'll buy that information for pennies from a data broker who inferred those conclusions based on other things you've done online. 3. Weblining for fun and profit If you've ever applied for a job, a loan, insurance, or just about anything else in the past couple of years, you probably started by going online and filling out a form. The site where you did that could easily have access to one of your profiles. If you've been tagged as a gay smoker by some data mining company, the employer or the bank won't have to ask you if you enjoy the occasional puff – they'll already know. Some online banks are already starting to use Facebook profiles as a way to identify poor credit risks. If your friends are deadbeats – or at least, fit the profile of likely deadbeats – you probably are one too. Why risk it, when it's safer to just issue an immediate rejection? In the real world, refusing to sell insurance or offer loans to residents of certain neighborhoods – typically containing a high percentage of minorities -- is called “redlining.” It's illegal, though difficult to prove. Online it's called “Weblining.” Aside from some regulated industries (like health and financial), Weblining is not illegal. And proving it? Good luck. This isn't just theoretical whining from privacy nut-jobs. Both the Network Advertising Initiative and the Digital Advertising Alliance have agreed to not collect or use tracking information “for the purpose of making an adverse determination of a consumer’s eligibility for employment, credit standing, health care treatment and/or insurance underwriting.” Bravo to the NAI and DAA for pro-actively adopting those restrictions. But these principles are voluntary and only apply to NAI and DAA members. What about the 600+ tracking companies that aren't members of the NAI or the DAA? What are they going to do with your data? Who's watching them? Who's going to stop them? If you're a fan of Slayer but you don't smoke cigarettes, will you still be shown a higher rate when you go to renew your health insurance online, just because the insurance company assumes you do? Or let's say you operate an 'exclusive' online club with a very restrictive membership policy. How hard would it be to exclude applicants for being of the wrong ethnic, sexual, or political persuasion? Not hard at all. 4. Two wrongs could still undo your rights As I've written about a few times before, online data profiles are often wildly inaccurate. You may be a spindly old crone who never leaves the house, but data tracking company X thinks you're a NASCAR dad who smokes cigars and eats nachos. You may be pegged as a trendy soccer mom when you are instead a manly intrepid reporter who is neither tarnished nor afraid. Multiple people may use the same browser, confusing the profilers. Or maybe you're clever and visit Web sites totally at random to pollute their data and throw them off the scent. It doesn't matter. You might receive benefits you otherwise wouldn't – like coupons for that big party size bag of Doritos. Or you might be needlessly penalized by a car insurance company that decides you're a curly fries-eating metal-head who can't be trusted to obey the posted speed limit. But your profile data could still be used to make decisions about you in invisible ways. It's a safe bet that tracking technology will get far more precise and accurate over time. Whether that's a comfort or a worry, I'm not sure yet. But I am sure we need a way to just say no to tracking, and for our choices to be honored. So How Do I Keep From Being Tracked? |
Archives
August 2018
Categories |









 RSS Feed
RSS Feed

